A Tool for Detecting Metamorphic Smart Contracts
A crucial Ethereum security presumption is that clever agreement code is immutable and for that reason can not be altered once it is released on the blockchain. In practice, some clever agreements can modification– even after they’ve been released. With a couple of creative techniques, you can produce metamorphic wise agreements that “ metamorphose” into something else– and by comprehending what makes them possible, you can discover them.
Metamorphic clever agreements are mutable, implying designers can alter the code inside them. These wise agreements posture a severe danger to web3 users who put their rely on code that they anticipate to keep up outright consistency, particularly as bad stars can exploit this shape-shifting capability. Think of an opponent utilizing the method to “carpet” individuals who are staking tokens in a wise agreement they do not recognize is metamorphic. Attacks based upon this and comparable properties might gear up fraudsters to victimize individuals and typically weaken rely on the complete guarantee of decentralized systems.
To examine whether a clever agreement consists of metamorphic homes, I constructed a basic Metamorphic Contract Detector( motivated by and structure on the initial work of Jason Carver, 0age, and others) Anybody can utilize the tool to inspect whether an offered agreement displays warnings that might suggest the capacity for metamorphism. The technique is not fool-proof: even if a wise agreement reveals a flag, does not imply it’s always metamorphic; and even if it does not, does not imply it’s safe. The checker simply uses a fast preliminary evaluation that an agreement may be metamorphic based upon possible signs.
Web3 users need to familiarize themselves with the hazards postured by metamorphic agreements so they can keep an eye out for and prevent possible attacks. Wallets and blockchain indexers can assist by alerting users prior to they engage with a wise agreement that might consist of metamorphic residential or commercial properties. This tool is meant to assist in both informing individuals about this possible hazard … and preventing it.
Detecting metamorphic clever agreements
The Metamorphic Contract Detector I developed evaluates 6 homes that might show if a clever agreement is metamorphic.
-
- Was recognized metamorphic code utilized to release the agreement? If understood metamorphic bytecode– the lower-level, virtual machine-readable code that Ethereum wise agreements, usually composed in Solidity, develop into after getting put together– appears in a deal for a provided clever agreement’s implementation, that’s a significant warning. In the areas that follow, we’ll go over one such example of metamorphic bytecode established by 0age. An essential caution: There are possibly numerous variations of metamorphic bytecode, that makes spotting all ranges hard. By scanning for widely known circumstances though, the detector removes low-hanging fruit for enemies who are simply copying and pasting existing examples.
- Can the wise agreement code self-destruct? To change the code in an agreement– a crucial action in developing a metamorphic agreement– a designer initially requires to erase pre-existing code. The only method to do this is by utilizing the SELFDESTRUCT opcode, a command that does precisely what it seems like– it eliminates all code and storage at a provided agreement address. The existence of self-destructing code in an agreement does not show that it is metamorphic; nevertheless, it provides an idea that the agreement may be metamorphic and it’s worth understanding, anyhow, whether agreements you’re depending on can obliterate themselves.
- Does the wise agreement contact code from somewhere else? If the wise agreement in concern can’t straight self-destruct, it might still have the ability to eliminate itself by utilizing the DELEGATECALL opcode This opcode permits a clever agreement dynamically to load and carry out code that lives inside another wise agreement. Even if the wise agreement does not consist of the SELFDESTRUCT opcode, it can utilize DELEGATECALL to fill self-destructing code from elsewhere. While the DELEGATECALL performance does not straight suggest if a clever agreement is metamorphic, it is a possible idea– and possible security concern– that’s worth keeping in mind. Be cautioned that this indication has the possible to raise numerous incorrect positives.
- Did another agreement release this agreement? Metamorphic agreements can be released just by other clever agreements. This is since metamorphic agreements are allowed by another opcode, functional just by other wise agreements, called CREATE2. (We’ll talk about CREATE2– how it works and why it matters– more in a later area.) This characteristic is among the least noticeable indications of possible metamorphism; it is a needed however inadequate prerequisite. Scanning for this quality is most likely to raise numerous incorrect positives– however it is important info to referred to as it can raise suspicions and supply a factor to inspect an agreement even more, particularly if the wise agreement includes the opcode explained next.
- Does the deployer agreement consist of the CREATE2 opcode? As pointed out above, release through CREATE2 is a vital prerequisite for metamorphism. If a deployer agreement consists of the CREATE2 opcode, that might show that it utilized CREATE2 to release the agreement in concern. If the deployer did certainly utilize CREATE2 to release stated agreement, while that does not indicate the agreement is always metamorphic, it does indicate that it may be metamorphic and it might be a good idea to continue with care and examine even more. Once again, beware incorrect positives: CREATE2 has lots of genuine usages, consisting of reinforcing ” Layer 2″ scaling services and making it much easier to produce wise agreement wallets that can enhance web3 user-onboarding and essential healing alternatives.
- Did the code modification? This is the most apparent inform, however it will just appear after a metamorphic agreement has actually currently changed. If the clever agreement’s code hash– a distinct, cryptographic identifier– is various than it was when the agreement was at first released, then it’s most likely the code was eliminated, changed, or modified. If the hashes no longer match, then something about the code has actually altered and the agreement may be metamorphic. This flag is the best indication of metamorphism, however it will not assist anticipate or preempt changing given that it just checks that it currently occurred.
In addition to developing an easy command line tool for the Metamorphic Contract Detector, I constructed some example clever agreements that show a fraud metamorphic agreement staking circumstance, which I explain in the next area. All the code is offered in this GitHub repository
How a harmful star can utilize metamorphic agreements to take individuals’s funds
Here is how somebody may utilize a metamorphic wise agreement as part of a rip-off.
First is the setup stage. The aggressor releases a clever agreement at a particular address on the blockchain utilizing 2 tools: metamorphic bytecode and the CREATE2 opcode. (We’ll broaden on both of these ideas later on.) The metamorphic bytecode then does what its name recommends and “morphs.” Here, it becomes a staking agreement where users can stake ERC-20 tokens. (Again, we’ll go over the information of this changing technique later on. Pledge!)
Next comes the bait and switch. Unwary users stake their tokens in this agreement, tempted by the possibility of making a yield or some other perk. The opponent then erases all the staking code and “state”– blockchain storage or memory– at this clever agreement address utilizing the SELFDESTRUCT opcode talked about in the previous area (It must be kept in mind that the tokens– which exist as part of a different ERC-20 agreement– continue, untouched by the self-destructed agreement.)
Finally, the rug-pull. The opponent recycles the exact same metamorphic bytecode utilized in the setup stage to “redeploy” a brand-new agreement. This brand-new agreement releases to the exact same address just recently abandoned by the self-destructing agreement. This time, nevertheless, the bytecode “morphs” (once again, we’ll discuss how later) into a harmful agreement that can take all the tokens staked at the agreement address. Fraud total.
The dangers that metamorphic wise agreements present are by now clearly obvious. You may still be questioning, how does this metamorphism technique in fact work? To comprehend that, you need to penetrate much deeper, to the bytecode-level.
How CREATE2 opens the possibility of metamorphism
CREATE2 is an opcode upgrade, presented to Ethereum in February 2019, that provides a brand-new method to release wise agreements.
CREATE2 provides designers more control over the release of their wise agreements than they formerly had. The initial CREATE opcode makes it hard for designers to manage the location address for a to-be-deployed clever agreement. With CREATE2, individuals can manage and understand the address of a specific clever agreement ahead of time, prior to in fact releasing it to the blockchain. This foreknowledge– plus some creative techniques– is what allows individuals to develop metamorphic wise agreements.
How can CREATE2 forecast the future? The opcode’s estimation is deterministic: as long as the inputs do not alter, the address figured out by CREATE2 will not alter. ( Even the tiniest modification will trigger the implementation to occur elsewhere.)
More granularly, CREATE2 is a function that integrates and hashes together a couple of components. It includes the address of the deployer (or sender): the starting clever agreement that acts as a moms and dad to the one to be produced. Next, it includes an approximate number offered by the sender (or “salt”), which permits the designer to release the exact same code to various addresses (by altering the salt) and avoids overwriting existing, similar agreements. It utilizes the keccak256 hash of some clever agreement initialization (” init”) bytecode, which is the seed that turns into a brand-new wise agreement. This hashed-together mix identifies an Ethereum address and after that releases the offered bytecode to that address. As long as the bytecode stays precisely the exact same, CREATE2 will constantly release the provided bytecode to the exact same address on the blockchain.
Here’s what the CREATE2 formula appears like. (Note: you’ll observe another aspect, a “0xFF,” in the example listed below. This is simply a continuous CREATE2 utilizes to avoid accidents with the preceding CREATE opcode.)
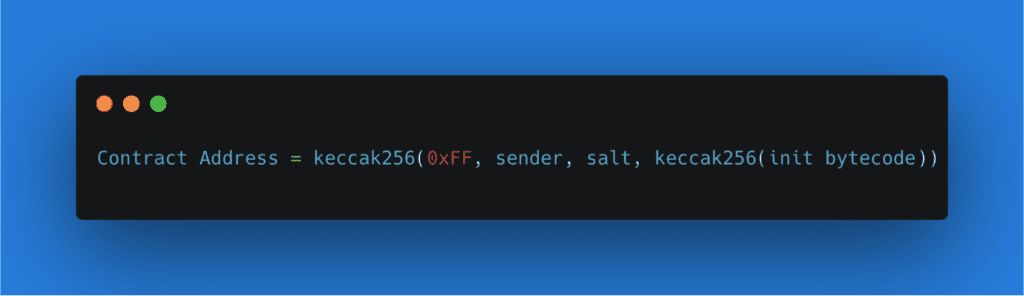
Now that we have a method to release code to a deterministic address, how is it possible to modification the code at that very same address? In the beginning, this might appear difficult. If you wish to release brand-new code utilizing CREATE2, the bytecode should alter, and for that reason, CREATE2 will release to a various address. What if a designer built the bytecode in such a method that it could “change” into various code when CREATE2 releases a clever agreement?
How a metamorphic agreement really works
The dish for turning a wise agreement into a metamorphic agreement requires 3 clever agreements in overall, each playing a special function.
One of these needed elements is the Metamorphic Contract Factory, the brain of the operation. This “Factory” is accountable for releasing the Metamorphic Contract along with another wise agreement called the Implementation Contract, so called due to the fact that its code ultimately ends up being executed inside the Metamorphic Contract. A subtle choreography in between these 3 agreements leads to metamorphism, as portrayed in the diagram listed below.
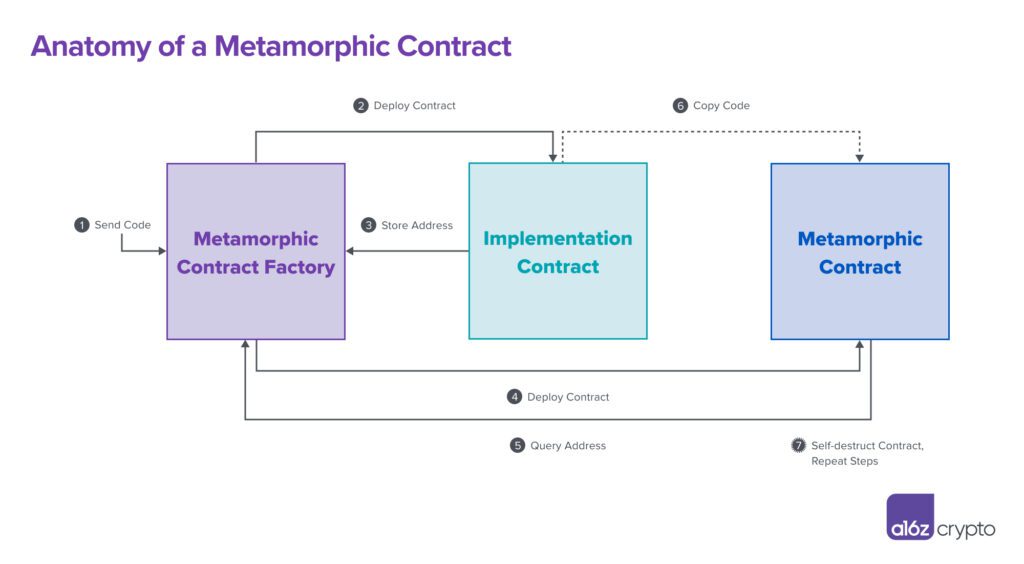
Let’s go over each action, 1-7, in information to brighten the operations at work.
Step 1: A designer sets whatever in movement
A coder creates some wise agreement code– the Implementation Contract bytecode– that will ultimately wind up in the Metamorphic Contract. The designer sends this code to the Metamorphic Contract Factory, a clever agreement whose primary function is to release other clever agreements. This action sets the whole Metamorphic Contract production procedure in movement.
Everything that follows is an outcome of this preliminary action. Steps 1 through 6 occur in one atomic deal on the blockchain, implying almost all at when. These actions can be duplicated over and over once again, advertisement infinitum, to change code inside the Metamorphic Contract and keep it constantly changing.
Step 2: Factory releases Implementation Contract
The very first agreement the Factory releases is the Implementation Contract, which consists of execution code. (Creative, we understand.) Consider the Implementation Contract as a packing dock, or waypoint, that holds some code prior to it ships to its last location, which will be, in this case, inside the Metamorphic Contract.
Step 3: Factory shops Implementation Contract address
After its implementation to the blockchain, the Implementation Contract will always exist at some blockchain address. The Factory shops this agreement address in its own memory (to be utilized later on, in Step 5).
Step 4: Factory releases Metamorphic Contract
The Factory releases the Metamorphic Contract utilizing CREATE2 and metamorphic bytecode. You can discover a technical, extensive walkthrough of how metamorphic bytecode works here, however suffice it to state that when metamorphic bytecode performs, it copies code from some other on-chain area– in this case, from the Implementation Contract– into the Metamorphic Contract. As we spoke about in the last area, given that CREATE2 is deterministic– as long as the very same sender, salt, and bytecode are utilized– then the Metamorphic Contract address remains the exact same no matter the number of times these actions are duplicated.
Below is an example of what metamorphic bytecode appears like, from the metamorphic repo by 0age. This is simply one example of metamorphic bytecode– possibly numerous variations exist, significantly making complex the detection of metamorphic agreements.
Step 5: Metamorphic bytecode questions Factory for Implementation Contract address
The metamorphic bytecode asks the Factory for the Implementation Contract address (as kept in Step 3). It does not matter if the address of the Implementation Contract modifications as long as the metamorphic bytecode that requests the address remains the very same. If the designer later on releases a brand-new Implementation Contract– such as a destructive one created to take tokens– it will always release at a various blockchain address, per Step 2. This has no effect on the Metamorphic Contract’s production.
Step 6: Implementation Contract code gets copied into the Metamorphic Contract
Using the blockchain address found out in Step 5, the metamorphic bytecode finds the code in the Implementation Contract and copies that code into the Metamorphic Contract’s regional storage. This is how the Metamorphic Contract shape-shifts: by copying code from the Implementation Contract.
Step 7: Rinse and repeat
A designer can duplicate Steps 1 through 6 over and over once again and change the code in the Metamorphic Contract with whatever they like by method of a brand-new Implementation Contract. All that’s required is to utilize the SELFDESTRUCT opcode– or, more deviously, DELEGATECALL opcodes that eventually lead to a SELFDESTRUCT– to eliminate the pre-existing code in the Metamorphic Contract. By duplicating the cycle with brand-new Implementation Contract bytecode, the Metamorphic Contract will, like magic, change!
Using this strategy for developing metamorphic agreements, a creative designer can continuously move the ground under web3 users’ feet. Consider, for instance, the fraud situation once again. A designer may initially release the Implementation Contract with token-staking code that, through the circuitous course portrayed in the graphic and elaborated in the actions above, winds up in the Metamorphic Contract. The fraudster might later on self-destruct this code and change it by releasing a brand-new Implementation Contract consisting of token- stealing code.
Whatever gets released in the Implementation Contract will eventually wind up in the Metamorphic Contract. That’s the essence of the technique.
Metamorphic clever agreements break the implicit web3 social agreement that what you see is what you get. Similar to the method the shell video game utilizes 3 moving cups to conceal a ball, the interaction of the 3 agreements in the production of a metamorphic agreement makes it tough to follow the agreement’s real function. The shell video game is an especially apt contrast due to the fact that self-confidence tricksters will frequently utilize deception and misdirection to guarantee they win. In the web3 variation, metamorphic agreement authors can likewise make the “ball”– the application code, that is– disappear (read: self-destruct), and they can change it with whatever they like.
The presence of metamorphic agreements implies it’s possible for web3 users to participate in agreements that can alter at will– that’s why this hazard is so essential to comprehend and prevent. My Metamorphic Contract Detector provides simply a primary step towards determining metamorphic agreements by the deception they utilize. There are numerous methods the detector might be enhanced in the future. By recursively examining the Factory (or deployer agreement) that produced the Metamorphic Contract, one might see if the Factory is itself metamorphic. This function would be a helpful addition to an updated variation 2 of the Detector.
It’s worth restating when again: This Detector tool is not fool-proof. The flags it captures aren’t all indicators of metamorphic capacity, however they do use hints. Recognizing these flags is simply the start for a more extensive questions. That’s why we broadened the Detector to look for flags that might quickly create incorrect positives, like the existence of CREATE2 or DELEGATECALL opcodes. If you have ideas for enhancing the tool or wish to develop on or contribute to this preliminary work, connect with me at [e-mail secured]
Analyze clever agreements for metamorphic characteristics utilizing the Detector tool and check out the GitHub repo for more
Editor: Robert Hackett @rhhackett
Acknowledgements: I wish to provide a HUGE shoutout and thank you to Robert Hackett, Eddy Lazzarin, Sam Ragsdale, Riyaz Faizullabhoy, Noah Citron, Mason Hall, and Daejun Park for important feedback and suggestions in making this post and tool come to life.
The views revealed here are those of the private AH Capital Management, L.L.C. (” a16 z”) workers priced estimate and are not the views of a16 z or its affiliates. Specific info consisted of in here has actually been gotten from third-party sources, consisting of from portfolio business of funds handled by a16 z. While drawn from sources thought to be dependable, a16 z has actually not separately validated such details and makes no representations about the long-lasting precision of the details or its suitability for a provided scenario. In addition, this material might consist of third-party ads; a16 z has actually not evaluated such ads and does not back any marketing material consisted of therein.
This material is attended to informative functions just, and ought to not be trusted as legal, service, financial investment, or tax recommendations. You need to consult your own consultants regarding those matters. Referrals to any securities or digital possessions are for illustrative functions just, and do not make up a financial investment suggestion or deal to supply financial investment advisory services. This material is not directed at nor desired for usage by any financiers or potential financiers, and might not under any situations be relied upon when making a choice to invest in any fund handled by a16 z. (An offering to invest in an a16 z fund will be made just by the personal positioning memorandum, membership arrangement, and other appropriate documents of any such fund and must be checked out in their totality.) Any financial investments or portfolio business discussed, described, or explained are not agent of all financial investments in lorries handled by a16 z, and there can be no guarantee that the financial investments will pay or that other financial investments made in the future will have comparable attributes or outcomes. A list of financial investments made by funds handled by Andreessen Horowitz (omitting financial investments for which the company has actually not supplied authorization for a16 z to reveal openly in addition to unannounced financial investments in openly traded digital possessions) is offered at https:// a16 z.com/investments/.
Charts and charts supplied within are for informative functions exclusively and need to not be trusted when making any financial investment choice. Previous efficiency is not a sign of future outcomes. The material speaks just since the date suggested. Any forecasts, price quotes, projections, targets, potential customers, and/or viewpoints revealed in these products go through alter without notification and might vary or contrast viewpoints revealed by others. Please see https:// a16 z.com/disclosures for extra essential info.